Go Beyond Your Wildest Dreams
On-demand keyless end-to-end encryption for timeless security. - Web 3 blockchain
Security Module as a Software Service (SMAASS) For B2B

How Secure Is your Data?
Your website is open to cyber attacks
You built an awesome website and continuously trying to grow steady traffic while trying to maintain customer relationship. We understand the hard work of growing and maintaining your brand. But you know your website could be vulnerable, right?
Every user is a suspect
The Sky's The Limit
We Created Solutions That Protect Online Privacy; Secure Businesses's And Client's Information.
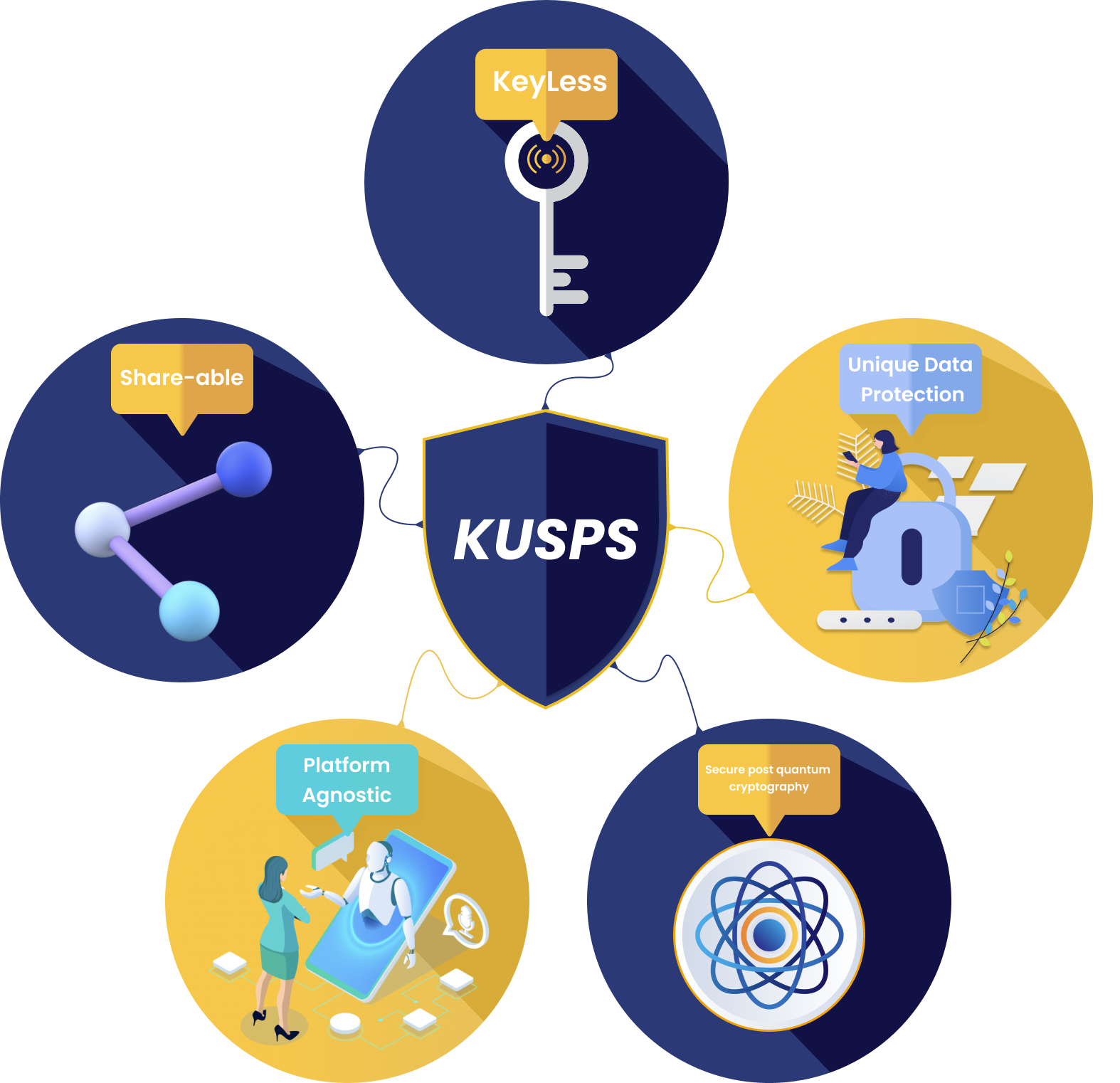
LokDon has built a robust, fast, low-cost, security module as a software service using patented keyless authentication and platform-agnostic internet protocols designed to keep your information a secret before and after you might have shared it.”
We Solve Real Problems
LokDon has everything you need to defend your website
Data Decentralization
Records are distributed across nodes. We have engaged an autonomous method or protocol allowing each user or node to keep its records
Autonomous Poly/Homomorphic Encryption
Encryption/decryption of all data with 2048 bits AES derivative. Just like any progressive development. This layer of LokDon technology is quite novel.
Friendly Documentation
Some of the support and extended features might not be free but a general use of the system in personal application is supported as it is.
General Use
It is readily available for use in all applications where data need to be secure. It comes with easy integration. You can incorporate this into a simple mobile application as well as complex enterprise software regardless of the OS platform.
Hides Data
The system remains secure and compliant to all sort of classified data while filtering unauthorized users. It covers all known standards, compliances (GDPR & CCPA) and most regulatory mandates or statues.
Indefatigable
Corporations and clients can modify the modes of operation to their liking and technical specification. This will stand any future rise in advanced encryption hacking techniques and /or analysis.
Our Strategies
LokDon has built a robust, fast, low-cost, security module as a software service using patented keyless authentication and platform-agnostic internet protocols designed to keep your information a secret before and after you might have shared it

Josiah J. Umezurike
Emma Morris
Meet Our Clients
They Believe In Us
We are proud to build partnership with reputable companies around the world.
We protect your privacy by destroying the cyber kill chain making your information secure 24/7








we love them
what our clients have to say


